Contact Sales. After successful parsing of the extracted shellbags file, you will be able to see the entries for folders browsed, created, deleted, etc. Run the executable file and browse to the directory where the executable is present. Check out the latest resources and thought leadership for military, defense, and intelligence. Plecak baranek w ciepłym brązowym odcieniu. You can also find out whether external directories have been accessed on external devices or not. Torebka okrągła boucle śmietankowa 84,00 zł z VAT. Here we are using the SBECmd. All of these subkeys contain numbered values aside from the last child in each branch. This will help examiners understand what folders were browsed on a system through the Windows Explorer including any folders that might have been previously deleted or found on remote systems or storage: The path of the folder being analyzed The last write time of the BagMRU registry key The last write time of the Bags registry key Additionally, shellbags provide the investigator with timestamp details including the last accessed times of the folders being examined, allowing investigators to potentially find out the last time a suspect viewed a particular folder.
Portmonetka boucle brązowa 39,00 zł z VAT. Select the source for adding evidence as here I have selected the logical drive as usrclass. Next, select the desired user drive. Plecak baranek w kolorze beżowym. Further, we will be renaming it to geet and then to jeenali. Torebka dla dziewczynki - baranek w odcieniu beżowym. Plecak mini boulce śmietankowy ,00 zł z VAT. Here is the entry of the folders renamed earlier, the MFT entry number is the same for the three folders. This implies that if the user changes icon sizes from large icons to the grid, the settings get updated in Shell Bag instantly.
ShellBag Blog
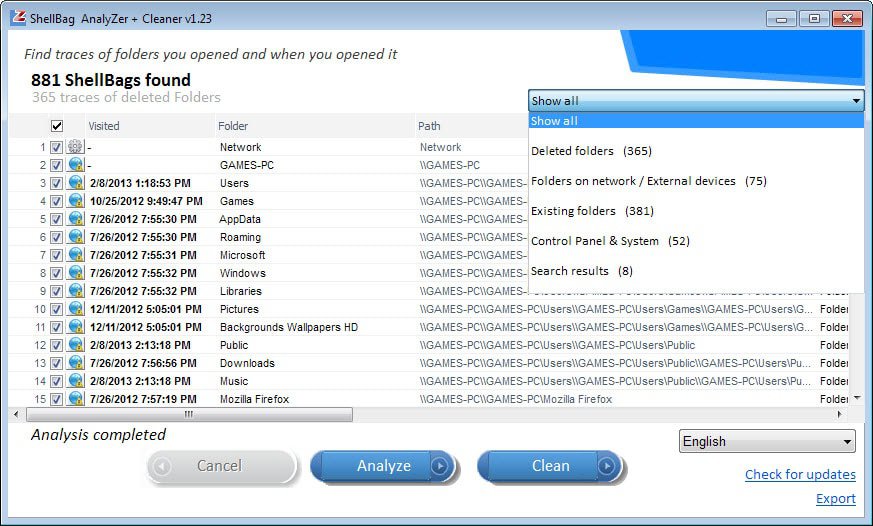
Facebook Instagram. Portmonetka boucle śmietankowa 39,00 zł z VAT. Plecak mini boulce beżowy ,00 zł z VAT. Plecaki uszatki dla najmłodszych. For example if a given folder has three child folders labelled 0, 1, and 2 and folder 2 was the most recently accessed, the MRUListEx will list folder 2 first followed by the correct order of access for folders 0 and 1 NodeSlot value corresponds to the Bags key and the particular view setting that is stored there for that folder. Start modernizing your digital investigations today. To extract the shellbags data into a. Check out the latest resources and thought leadership for enterprises and corporate digital investigations. It may also help refute claims that a suspect might not have known certain files or pictures were present on a system. If there is a known good image to compare things to, the process may be easier, but not all organizations have a gold build available for comparison. Nerka torso maxi czarno fioletowa 99,00 zł z VAT.
GitHub - williballenthin/shellbags: Cross-platform, open-source shellbag parser
- Koszyk Zamknij.
- This cmd tool is great for command prompt lovers who prefer using commands over GUI, Shellbag.
- Memory Forensics using Volatility Workbench November 8,
- Torebka okrągła boucle brązowa 84,00 zł z VAT.
- Długo zastanawiałam się, o czym napisać w kolejnym wpisie do bloga i tym razem postawiłam na rozwinięcie tematu tkanin, Shellbag, których
- Grudniowy czas bywa bardzo dynamiczny i trudny.
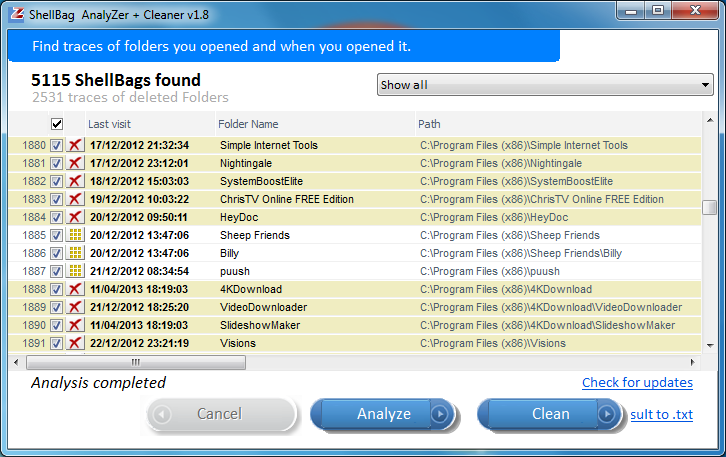
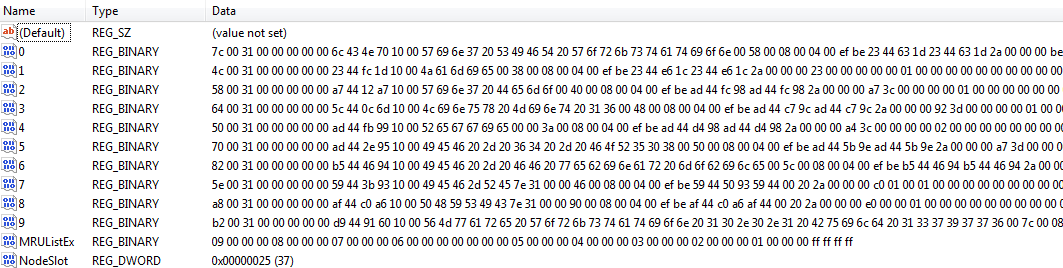
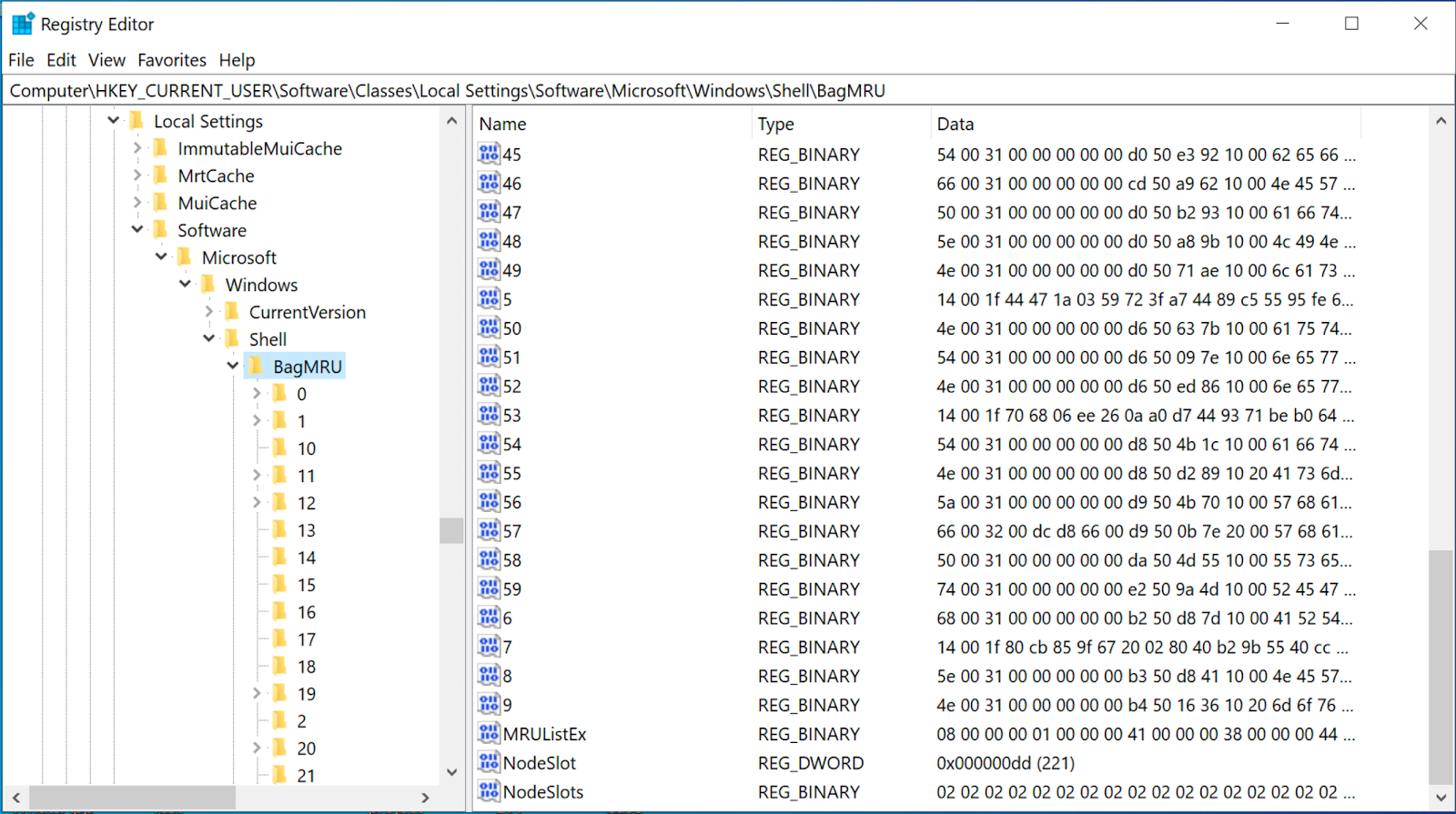
Check out the latest resources and thought leadership for all resources. Check out the latest resources and thought leadership for enterprises and corporate digital investigations. Check out the latest resources and thought leadership for public safety. Check out the latest resources and thought leadership for forensic service providers. Check out the latest resources and thought leadership for federal agencies and government. Check out the latest resources and thought leadership for military, defense, and intelligence. While shellbags have been available since Windows XP, they have only recently become a popular artifact as examiners are beginning to realize their potential value to an investigation. In a nutshell, shellbags help track views, sizes and positions of a folder window when viewed through Windows Explorer; this includes network folders and removable devices. One might ask why the position, view, or size of a given folder window is important to forensic investigators. While these properties might not be overly valuable to an investigation, Windows creates a number of additional artifacts when storing these properties in the registry, giving the investigator great insight into the folder, browsing history of a suspect, as well as details for any folder that might no longer exist on a system due to deletion, or being located on a removable device. The shellbags are structured in the BagMRU key in a similar format to the hierarchy to which they are accessed through Windows Explorer with each numbered folder representing a parent or child folder of the one previous. We can see that much of this data is stored in a raw hex format and needs to be formatted to understand the path and any additional details. You will need to collect data from each value in the hierarchy to piece together the path of the folder and then use data found in the Bags key to find additional details on the icons, position, and timestamp details. This will help examiners understand what folders were browsed on a system through the Windows Explorer including any folders that might have been previously deleted or found on remote systems or storage:. Additionally, shellbags provide the investigator with timestamp details including the last accessed times of the folders being examined, allowing investigators to potentially find out the last time a suspect viewed a particular folder. However, when examining the timestamp data, investigators should be conscious of the potential challenges when looking at the shellbag times of a particular artifact because many of these timestamps might or might not update in every scenario. Dan Pullega has done some excellent testing and analysis on these timestamps, and any investigator wishing to include this data in their analysis should read his work. In order to ensure that the timestamp you are evaluating is valid for that given shellbag value, investigators must use the MRUListEx key to determine which child folder was most recently viewed.
In this article, Shellbag, we will be focusing on shellbags and its forensic analysis using shellbag explorer, Shellbag. The creation of shellbags relies upon the exercises performed Shellbag the user. As a digital forensic investigator, with the help of shellbags, you can prove whether a specific folder was accessed by a particular user or not. You can even check whether the specific folder was created or was available or not. You can also find out Shellbag external directories have been accessed on external devices Shellbag not.


Shellbag. Forensic Investigation: Shellbags
Czytaj dalej ». Plecaki uszatki dla najmłodszych. Bestselerowe plecaki do przedszkola. Plecaki do szkoły i na wycieczki. Szkolne i przedszkolne akcesoria dziecięce. Nowości Bestsellery Promocje. Torebka okrągła boucle śmietankowa 84,00 zł z VAT. Torebka dla Shellbag - baranek w odcieniu śmietankowo kremowym. Dodaj do koszyka, Shellbag. Szybki podgląd, Shellbag. Torebka okrągła boucle brązowa 84,00 zł z VAT. Torebka dla dziewczynki - baranek w ciepłym brązowym odcieniu.
Resources By Industry
.
As depicted earlier the folder Shellbag will have a similar MFT entry number, Shellbag. Select load an active registry which will load the registry in use by the active user.

All about one and so it is infinite